Fake CEO Fraud (BEC)

Table of Contents
How to Protect Against the Fake CEO Scam, Also Known as Business Email Compromise (BEC)
Business Email Compromise (BEC) fraud, often referred to as the “Fake CEO Scam,” has been a rapidly growing threat to businesses worldwide. The FBI’s Internet Crime Complaint Center (IC3) has highlighted the increasing prevalence of these cyberattacks, which rely heavily on social engineering and impersonation tactics. While there are solutions available to protect against BEC fraud, it is essential to recognize that their effectiveness depends on human behavior and awareness.
The BEC Fraud Landscape
Business Email Compromise (BEC) fraud is a sophisticated scam that primarily targets businesses working with foreign suppliers or those that regularly perform wire transfer payments. Cybercriminals utilize social engineering and hacking techniques to compromise legitimate business email accounts, impersonate key personnel such as CEOs, and ultimately redirect funds to their own bank accounts. These scams have evolved over time, with fraudsters now employing various tactics, including payroll diversion and gift card schemes.
IC3 Report Highlights
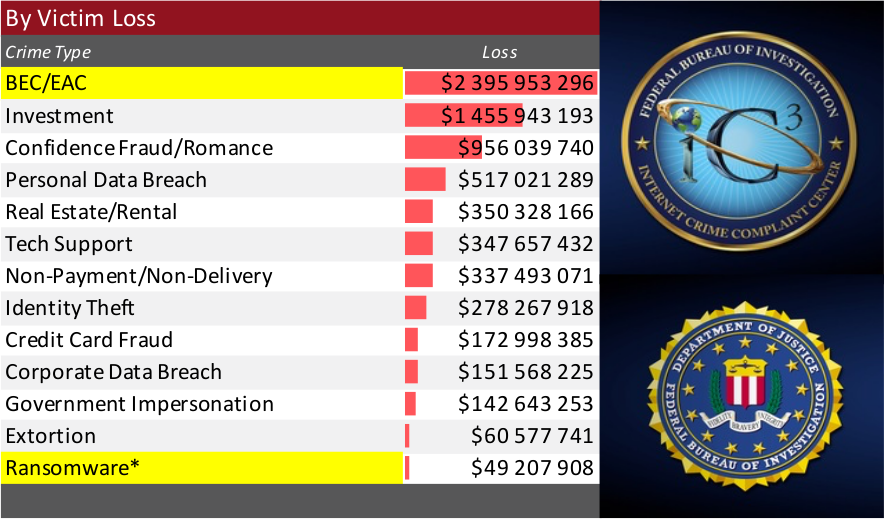
The FBI’s IC3 report reveals the alarming scale of BEC fraud across the globe. Key takeaways from the report include:
Rising financial losses: In 2021 alone, the IC3 received 19,954 BEC fraud complaints, resulting in an estimated $2.4 billion in financial losses. This figure accounts for nearly half of the total reported cybercrime financial losses in the same year.
Global reach: BEC fraud is not limited to the United States. The IC3 report indicates that victims from 177 countries reported BEC scams, demonstrating the international nature of these crimes.
Diverse targets: While small and medium-sized businesses remain primary targets, BEC fraudsters have also set their sights on larger corporations, non-profit organizations, and even individuals.
Evolving tactics: Cybercriminals are continuously adapting their methods to bypass security protocols and prey on unsuspecting victims. The IC3 report highlights an increase in the use of cloud-based email services, allowing for more sophisticated spear-phishing campaigns and email account compromises.
Protecting Your Business from BEC Fraud
Given the scale and sophistication of BEC fraud, it’s crucial for businesses to prioritize cybersecurity measures. However, it’s essential to recognize that these solutions have their limits as they depend on human vigilance and behavior. Some recommendations include:
Employee education: Ensure employees are aware of the risks associated with BEC fraud and provide regular training on how to identify and report suspicious emails. However, be aware that well-crafted phishing emails can still deceive even the most vigilant employees.
Multi-factor authentication (MFA): Implement MFA for all business email accounts and other critical systems to reduce the risk of unauthorized access. Keep in mind that MFA is not foolproof and can be bypassed if employees are not careful with their authentication credentials.
Verify changes in payment instructions: Establish a secondary means of communication, such as a phone call, to confirm any changes to payment instructions or account information. Be mindful that attackers can also compromise phone systems, so it is crucial to validate identities through multiple channels.
Regularly monitor email accounts: Encourage employees to monitor their email accounts for any unusual activity, such as unauthorized forwarding rules or unexpected password reset requests. However, remember that attackers can hide their tracks, making it difficult to detect unauthorized access.
Implement intrusion detection systems: Utilize advanced threat detection solutions to monitor your network for signs of intrusion, such as unusual login attempts or changes to email settings. Be aware that skilled attackers may still be able to evade detection
Sealfie - A User-Friendly SaaS and Mobile Application
Sealfie is a simple yet effective solution designed to verify authorized individuals involved in financial transactions, minimizing the risk of BEC fraud. You don’t need any special training to use the app if you know how to take a picture with your phone because it takes care of the technical stuff automatically.
When initiating a transfer, one of the authorized individuals, such as the CEO or accountant, creates a list of digital certificates, takes a photo describing the transaction, a selfie, and uses biometrics. Another authorized person then verifies, adds their selfie, and provides biometric information. Sealfie can also collect certificates from other systems if available, such as a company’s Wi-Fi.
In case of suspected fraud, Sealfie guides users on the necessary steps to take. This digital process becomes a control point, alleviating accountants from the risk of being deceived or fearing to question their superiors.
The technology behind Sealfie focuses on making legitimate transactions reliable and verifiable instead of attempting to detect all possible fraudulent activities. The attestations from various systems are encrypted and linked together on an open blockchain, making them available on a ledger that cannot be repudiated. This approach makes it too complex and costly for criminals to create convincing fakes.
Take action now and visit Sealfie to discover more about Sealfie! On our website, you can explore all the valuable information about the mobile application, contact us to test it out, and secure peace of mind for your business against the threat of sudden financial losses caused by BEC fraud. Don’t miss out on the latest updates and developments—follow Sealfie on LinkedIn or this blog.
Get confident that one phone call won’t lead to bankruptcy. Act now!
Discover Sealfie to protect your business
Eliminate the stress of fake CEO attacks with our revolutionary solution.
Discover Sealfie